Integrate Okta IAM with Dune Security
Follow these steps to implement the Okta API integration with Dune Security.
Option A (Preferred):
Guide to Creating a Service Role for Dune API Integration in Okta
This guide provides step-by-step instructions to create a service role in Okta for integrating with Dune Security through API.
.png?width=670&height=355&name=image%20(27).png)
Step 1: Access the Okta Admin Console
- Log in to your Okta Admin Console.
Step 2: Navigate to the Security Tab
- In the Admin Console, open the Security tab.
Step 3: Access the Administrators Section
- Under the Security tab, click on "Administrators".
Step 4: Create a New Role
- In the Administrators section, click on "Roles".
- Click on "Create Role" to initiate the creation of a new role.
Step 5: Configure the Role
- Name the Role: Enter the name "Dune API Integration".
- Assign Permissions:
- Search for and add the following permissions:
- "View users and their details"
- "View groups and their details"
- "View roles, resources, and admin assignments"
- "View Applications and their details"
- Search for and add the following permissions:
Step 6: Save the Role
- Once the necessary permissions have been added, click on "Save" to finalize the role creation.
Step 7: Create the API Token
- After saving the role, create an API token using the newly assigned "Dune API Integration" role. This token will be used for secure communication between Dune Security and your Okta environment.
Optional Step: Device Scope Early Access
If you are interested in utilizing the device scope, which is currently available in early access, follow these steps:
- Enable the Device Scope: Enable the device scope by following the instructions provided here.
- Assign the Necessary Scopes: Ensure that the required device scopes are granted to the "Dune Integration" user that was previously created.
For further details about device scopes, please refer to this link: Okta Device Permissions.
By following these steps, you will have successfully created a service role in Okta specifically tailored for Dune API integration, ensuring secure and efficient access management.
Option B:
Create and configure Okta API tokens for integration with Dune Security

Step 1: Access the Admin Console
- Navigate to Security Settings:
- Open the Okta Admin Console.
- Go to Security > API.
Step 2: Create an API Token
-
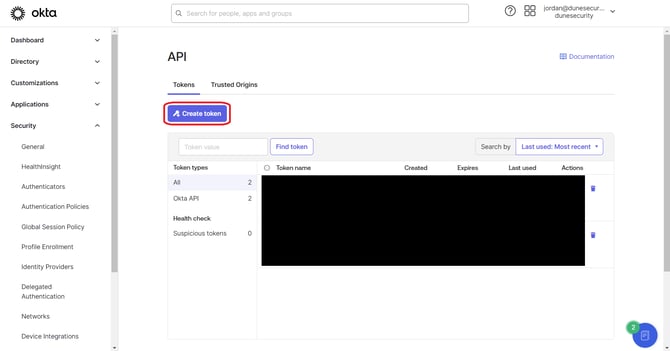
Open the Tokens Tab:
- Click on the Tokens tab.
-
Generate a New Token:
- Click Create Token.
- In the "What do you want your token to be named?" field, enter Dune Security Implementation.
- In the API calls made with this token must originate from? field, enter the following IP
34.203.66.28. - Click Create Token.
-
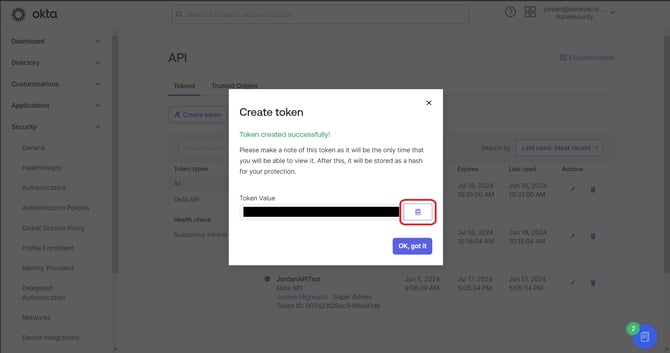
Save the Token:
- A message "Token created successfully!" will appear along with the token value.
- Click Copy to clipboard to save the API token.
- Store the token in a secure location, as you will be unable to access this token value in the future.
Step 3: Share the Token with Dune Security
- Provide Token to Dune Administrator:
- Follow any additional steps necessary to securely share this token with a Dune Administrator.
By following these steps, you will have successfully created and configured Okta API tokens for seamless integration with Dune Security. For further assistance, contact Dune Security Support.
Note: Always store your API token securely and limit access to it to ensure the security of your integration. This process gives Dune Security full access to your Okta environment.
Dune Security's Okta API Integration: Essential Permissions and Use Cases
To integrate Dune Security with Okta through the API, specific permissions are required to ensure proper functionality and security monitoring. Below are the API endpoints, the required scopes, and the use cases for each permission:
1. Group Management: /api/v1/groups*
- Scope Required:
okta.groups.read - Purpose: Allows the application to read group details and membership information.
- Use Case for Dune Security:
- Monitoring Unauthorized Group Changes: Detect suspicious group membership changes, such as users being added to privileged groups without the expected workflows.
- Tracking Group Creation/Deletion: Identify unexpected creation or deletion of groups, which could indicate a potential breach or misconfiguration.
- Audit Privileged Groups: Monitor privileged groups (like admin groups) for unusual access patterns or membership changes.
2. Device Management: /api/v1/devices*
- Scope Required:
okta.devices.read - Purpose: Allows the application to read device details registered with Okta.
- Use Case for Dune Security:
- Identify Unusual Device Registrations: Detect when new devices are registered unexpectedly or outside typical usage patterns.
- Track Device Activity: Monitor device activity to identify suspicious behaviors, such as access from unusual locations or devices not typically associated with a user.
- Flag Unauthorized Device Removals: Detect when devices are deregistered unexpectedly, which could signal an attempt to evade security controls.
3. Log Events: /api/v1/logs
- Scope Required:
okta.logs.read - Purpose: Allows the application to read Okta log events.
- Use Case for Dune Security:
- Track Unusual Login Patterns: Monitor login attempts, especially focusing on anomalies like failed logins, logins from unusual locations, or logins outside typical working hours.
- Audit Admin Activity: Analyze log data for any unusual admin actions, such as privilege escalations or unexpected configuration changes.
4. User Management: /api/v1/users
- Scope Required:
okta.users.read - Purpose: Allows the application to read user details and manage user accounts.
- Use Case for Dune Security:
- Monitor User Creation/Deletion: Detect unauthorized user creation or deletion, which could indicate malicious activity.
- Identify Inactive Accounts: Track accounts that haven't been used for a long time, which could be targets for compromise.
- Detect Role or Profile Changes: Identify any unauthorized changes in user roles or attributes, which could indicate potential privilege escalation or user impersonation.
5. Device Scope Early Access (Optional): /api/v1/devices*
- Scope Required:
okta.devices.read - Purpose: The device scope is currently available in early access, allowing the application to read detailed device information registered with Okta.
- Use Case for Dune Security:
- Enhanced Device Monitoring: Utilize advanced integrations and analysis engines developed by Dune Security to provide deeper insights into device-related activities.
- Identify Unusual Device Registrations: Detect when new devices are registered unexpectedly or outside typical usage patterns.
- Track Device Activity: Monitor device activity to identify suspicious behaviors, such as access from unusual locations or devices not typically associated with a user.
- Flag Unauthorized Device Removals: Detect when devices are deregistered unexpectedly, which could signal an attempt to evade security controls.
- Action Required:
- Enable the Device Scope: Enable the device scope by following the instructions provided here.
- Assign Scopes: Ensure the necessary scopes are granted to the "Dune Integration" user that was previously created.
- Learn More: For detailed information about device scopes, refer to the Okta Device Permissions page.
Summary of Required Permissions:
To enable these functionalities, the following Okta API scopes are necessary:
okta.groups.readokta.devices.readokta.logs.readokta.users.read
These permissions allow Dune Security to effectively monitor and enhance your organization's security posture by integrating with Okta and leveraging its data for risk management.
How Dune Security Safely Secures Data
Customer-Specific Security Policies
We collaborate closely with our clients to implement tailored security measures that align with their unique needs and risk profiles. This includes deploying custom encryption keys and defining data retention policies that meet your specific requirements.
Receiving Secrets
We ensure the secure transmission of secrets, API keys, and JSON configurations through either the Dune Security platform's secure portal or Box, a trusted file-sharing application. Both methods are designed to uphold the highest standards of security and confidentiality.
Storing Secrets
Secrets received through our platform are automatically stored in AWS Secrets Manager, ensuring that no keys or secrets are retained, even temporarily. For secrets shared via Box, they are securely transferred to AWS Secrets Manager, after which the Box instance is automatically deleted to eliminate any trace of the secret.
Application Secrets Handling
Keys and secrets are only accessed when absolutely necessary. We do not store them in environment variables or configuration files, reducing the risk of exposure.
Encryption
All data, whether in transit or at rest, is encrypted using industry-leading encryption standards. We employ AES-256 for data at rest and TLS 1.2+ for data in transit, ensuring that your sensitive information is continuously protected.
Data Retrieval
API requests for data querying are processed from a single, static IP address, enabling you to whitelist this IP for secure access to your sensitive resources. Additionally, we can configure custom HTTP headers to streamline the whitelisting process if required.
Data Processing
We handle data with care, adhering to API rate limits while securely storing and processing user data. All communications are encrypted via HTTPS, and our internal data processing engines operate under a strict zero-trust architecture. We follow the principle of least privilege, ensuring that data processing is performed securely. Upon request, all stored secrets and user data can be promptly deleted.
Continuous Monitoring
Our systems are under continuous surveillance to detect and respond to security threats in real-time. Automated alerts and response mechanisms are in place to swiftly mitigate any risks.
.png?width=670&height=358&name=image%20(29).png)
.png?width=670&height=353&name=image%20(30).png)